Huawei Mate30 loses SafetyNet certification, Google Apps install workaround

Earlier today, well-known developer John Wu — the name behind Android's current go-to root solution Magisk — penned an explanation over on Medium for precisely how the Mate 30's Google apps workaround worked. It was a pretty interesting read for folks interested in the minutiae of Android, as parts of it are a bit concerning from a security perspective. Based on the timing, it seems like it may have also worried some other folks as well, as the site hosting the installer APK for the Play Store workaround has been taken down.
Play Store workaround
There was more than a little concern over the "LZ Play" app initially, as it was able to finagle some pretty extreme administrator-level permissions. A closed-source, unknown, third-party app with access to block and allow app installation silently is precisely the sort of thing that raises red flags for those interested in security.
I did not pay attention to the "How to install gapps on the P30 Pro!" guides that were published last week, but GOOD LORD! You people were recommending users install an ADMINISTRATOR app from an unknown third-party? That is outrageously dangerous. Never install this. twitter.com/maple3142/stat…
18 people are talking about this
Unfortunately, LZ Play's workaround was basically a requirement for anyone interested in accessing the Play Store via their Mate 30-series device, as Huawei wasn't able to secure an exemption to the US' ban against the company and the bootloader of the device can't be unlocked to flash new apps to the system partition yourself. Without an official method, the LZ Play workaround was a popular choice, though it raised a few eyes when it came to security.
Undocumented APIs made public
I won't parrot John Wu's post in its entirety myself, as he does a good job of explaining the details in a generally accessible way, but the short version is that the LZ Play app uses a set of undocumented APIs Huawei has hidden in the Mate 30's software that amount to a sort of "backdoor," allowing non-system apps access to elevated permissions and privileges.
This isn't dangerous in the sense that anyone can access those undocumented APIs, they can't. According to Wu, without a signing key granted by Huawei, apps can't access the APIs, and Huawei only gives its blessing after an application process that requires the developer submit the app for approval. (All of that is described here, according to Wu, in Chinese.)
Permissions spotted by Wu in the LZ Play app, including two with no documentation.
While the APIs can't be used by just anyone, what is ultimately concerning is the fact that this circumvents part of the traditional Android security model, giving Huawei and developers it approves of a "backdoor" to system-level permissions from outside the system partition, where they aren't subject to the same security. And like any backdoor, it's technically possible that Huawei could use it for other things, approve access for questionable entities, or the security/certification it relies on could leak or be compromised in the future — though it still requires user action, even in that case, to work.
Essentially, the undocumented API's/backdoor and any apps like LZ Play that are using it should be as trustworthy as Huawei itself (however you may personally feel about that).
Site gets taken down
John Wu's explanation appears to have caught some other critical eyes as well, as shortly after it made the rounds earlier today, the site hosting the LZ Play app was taken down. We aren't sure if it was taken down by the developer behind the app (someone named QiHoo Jiagu, according to Wu) or the site's hosting service Alibaba. It's possible that Huawei was concerned regarding the bad press circulated about the technical details and sent the project or its host the Chinese equivalent of a cease and desist — though, presumably, the app would have needed Huawei's blessing in the first place to work.
Whatever the cause or explanation, lzplay.net is down, and the Mate 30's workaround for the Google Play Store has disappeared with it. In the meantime, folks interested in installing Google's apps onto their devices will probably just find even less trustworthy sources for the LZ Play app now that it's already out in the wild.
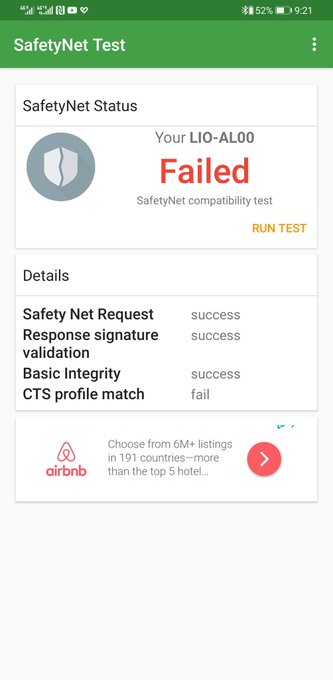
Shortly after publication, our friends at Android Central noticed that the Huawei Mate 30 no longer passes Google's SafetyNet security test:
Soooo uhh this is new.
Since today's developments, Mate 30 Pro now fails SafetyNet. Last week it passed.
What the what
101 people are talking about this
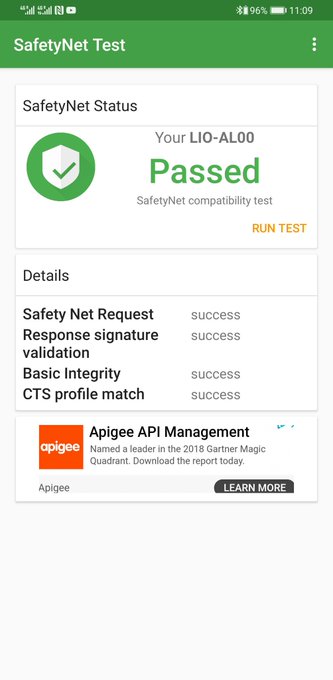
It's a little odd that the Mate 30 Pro passed SafetyNet to begin with. While some of the inner workings behind SafetyNet are unknown, it's supposed to work by comparing a signature generated on the phone with "reference data for approved Android devices" held by Google. While that doesn't mean that Google necessarily has to coordinate with Huawei to get that data in a way that might violate the current trade ban, it does imply the possibility. Google, as a US company, isn't supposed to be playing that sort of pattycake with Huawei.
This could simply be an error that we'll see restored in the future, and it could be that OEMs can submit information to Google for SafetyNet without violating any entity list trade bans. But it is more than a little suspicious that all this is happening on the same day.




Comments
Post a Comment